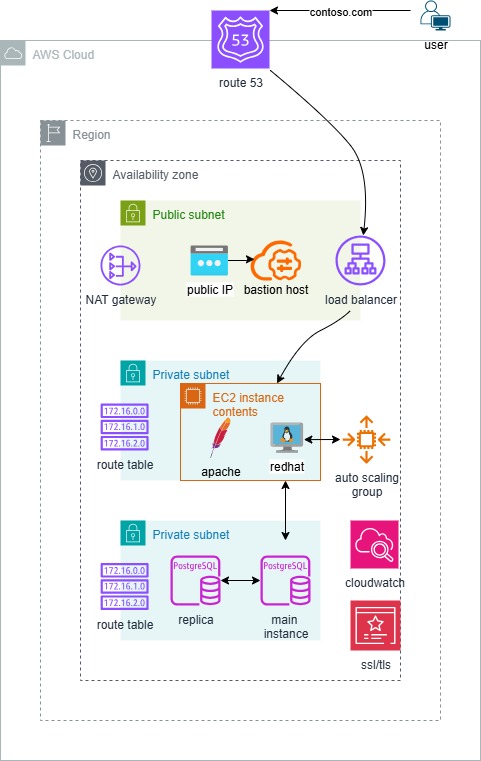
Launch type: Serverless | Template: Cloudfront | Security: Low | Language: HCL
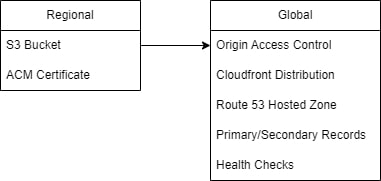
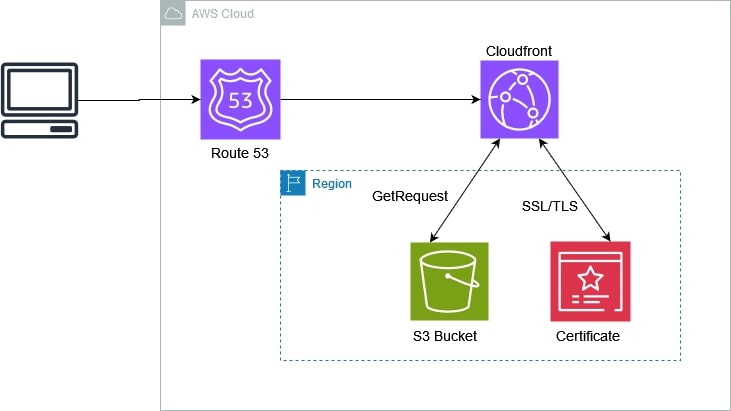
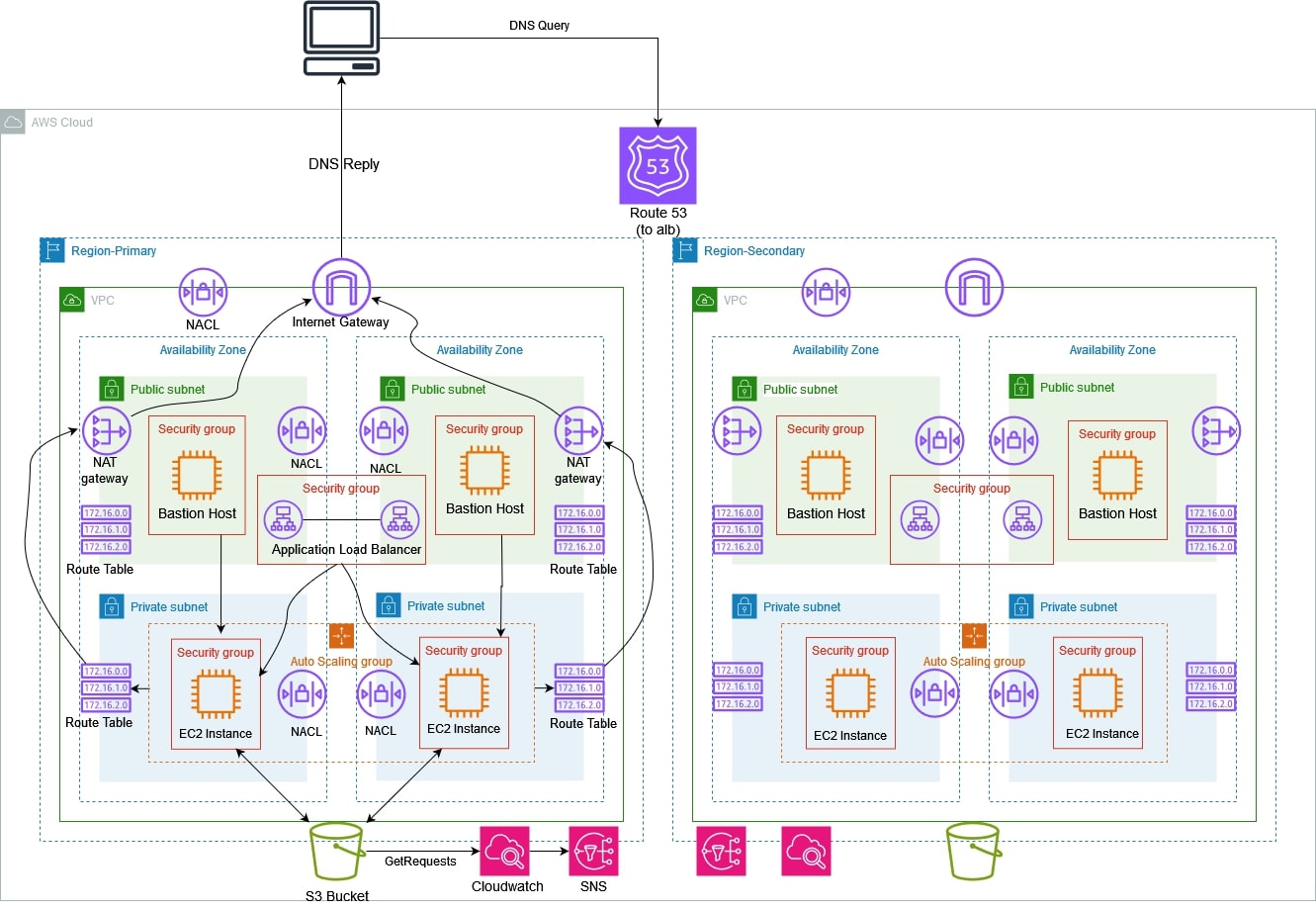
- S3 bucket will share static website files with server-side encryption enables for all objects. Versioning is automatically enabled to prevent accidental deletion.
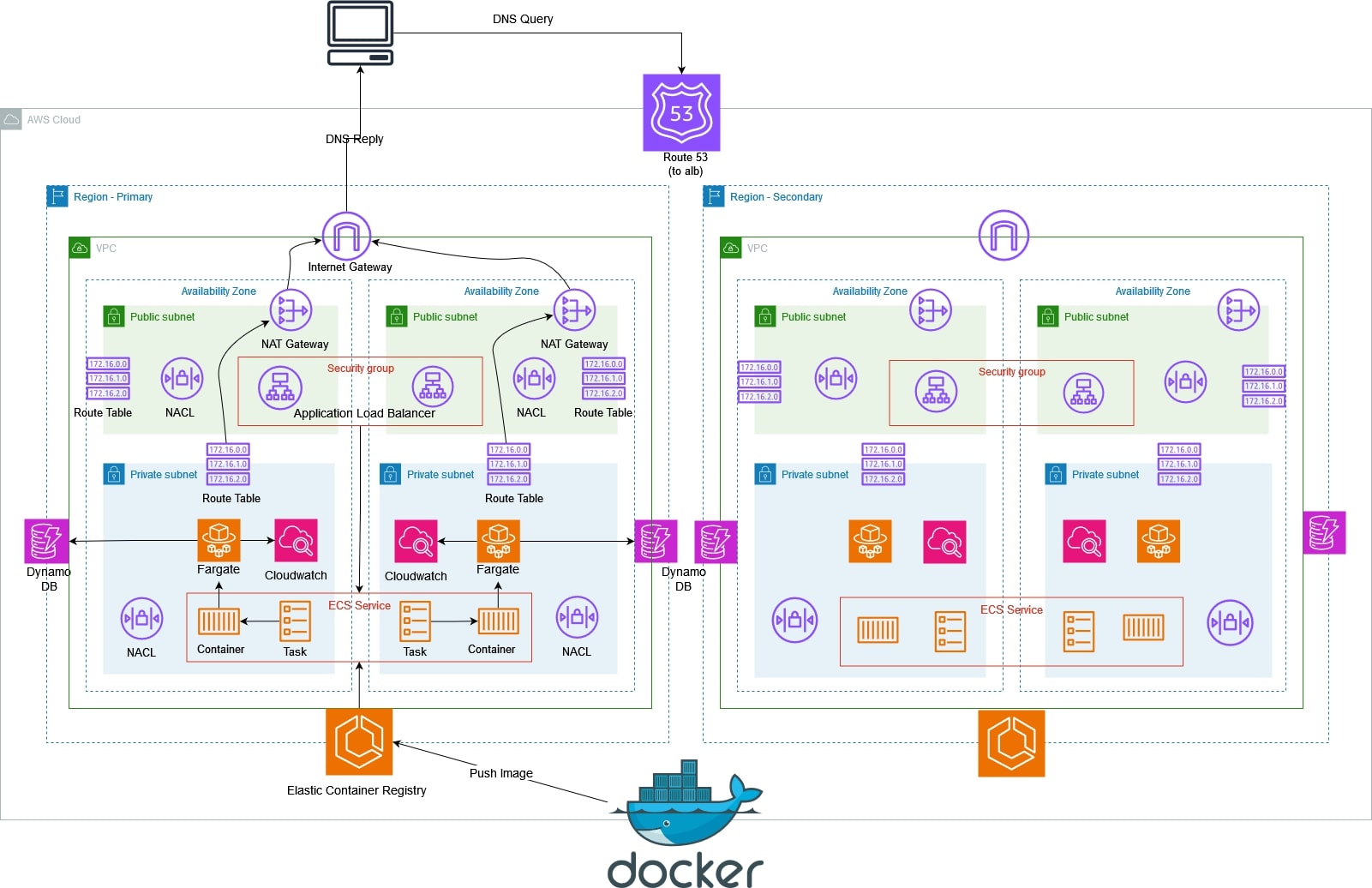
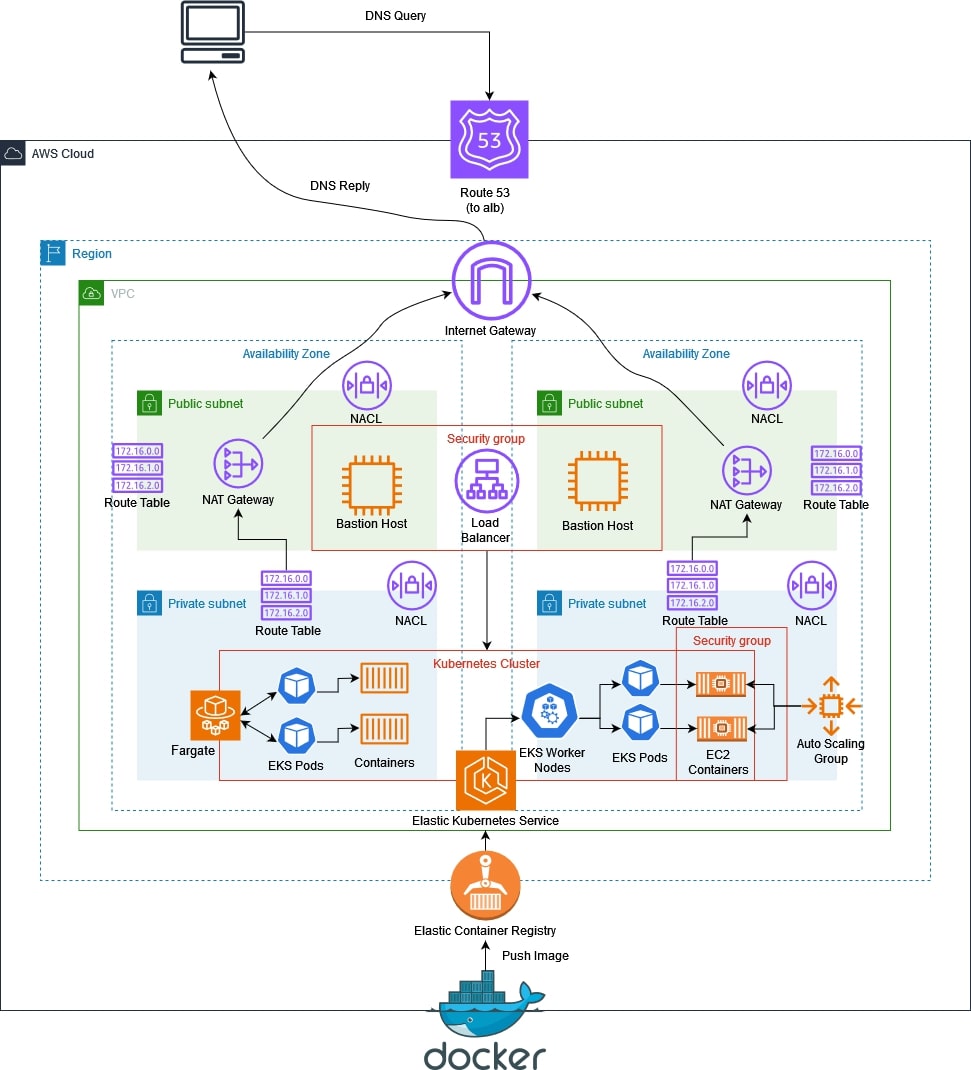
- Route 53 creates primary and secondary records to route traffic based on health checks.
- Cloudfront creates a distribution to serve static web pages from the s3 bucket. Configured with a TLS Certificate from AWS.
Description
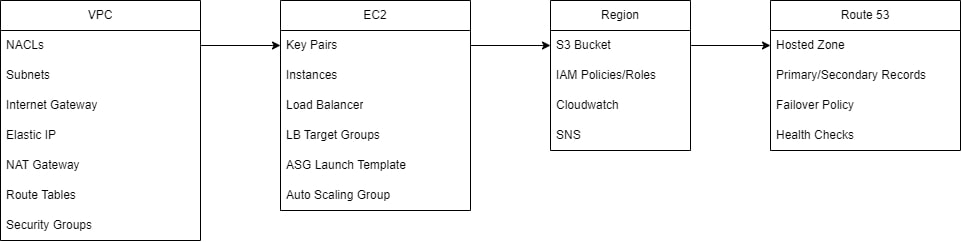
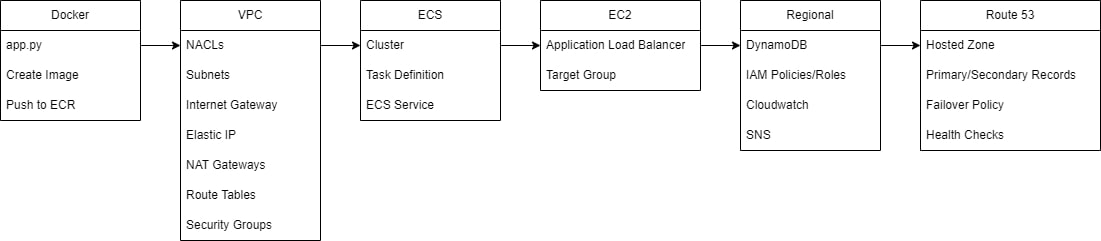
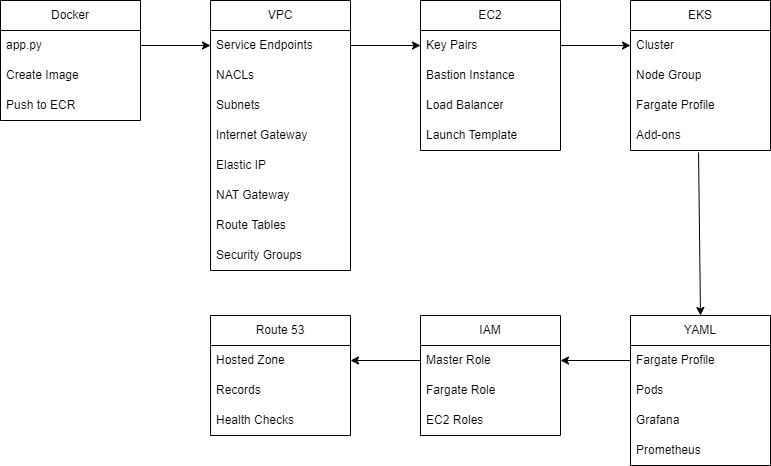
Build Order